Antivirus scanning order
The antivirus scanning function includes various modules and engines that perform separate tasks.
Proxy-based antivirus scanning order
The following figure illustrates the antivirus scanning order when using proxy-based scanning. The first check for oversized files/email is to determine whether the file exceeds the configured size threshold. The uncompsizelimit check is to determine if the file can be buffered for file type and antivirus scanning. If the file is too large for the buffer, it is allowed to pass without being scanned. For more information, see the config antivirus service command. The antivirus scan includes scanning for viruses, as well as for grayware and heuristics if they are enabled.
|
|
File filtering includes file pattern and file type scans which are applied at different stages in the antivirus process. |
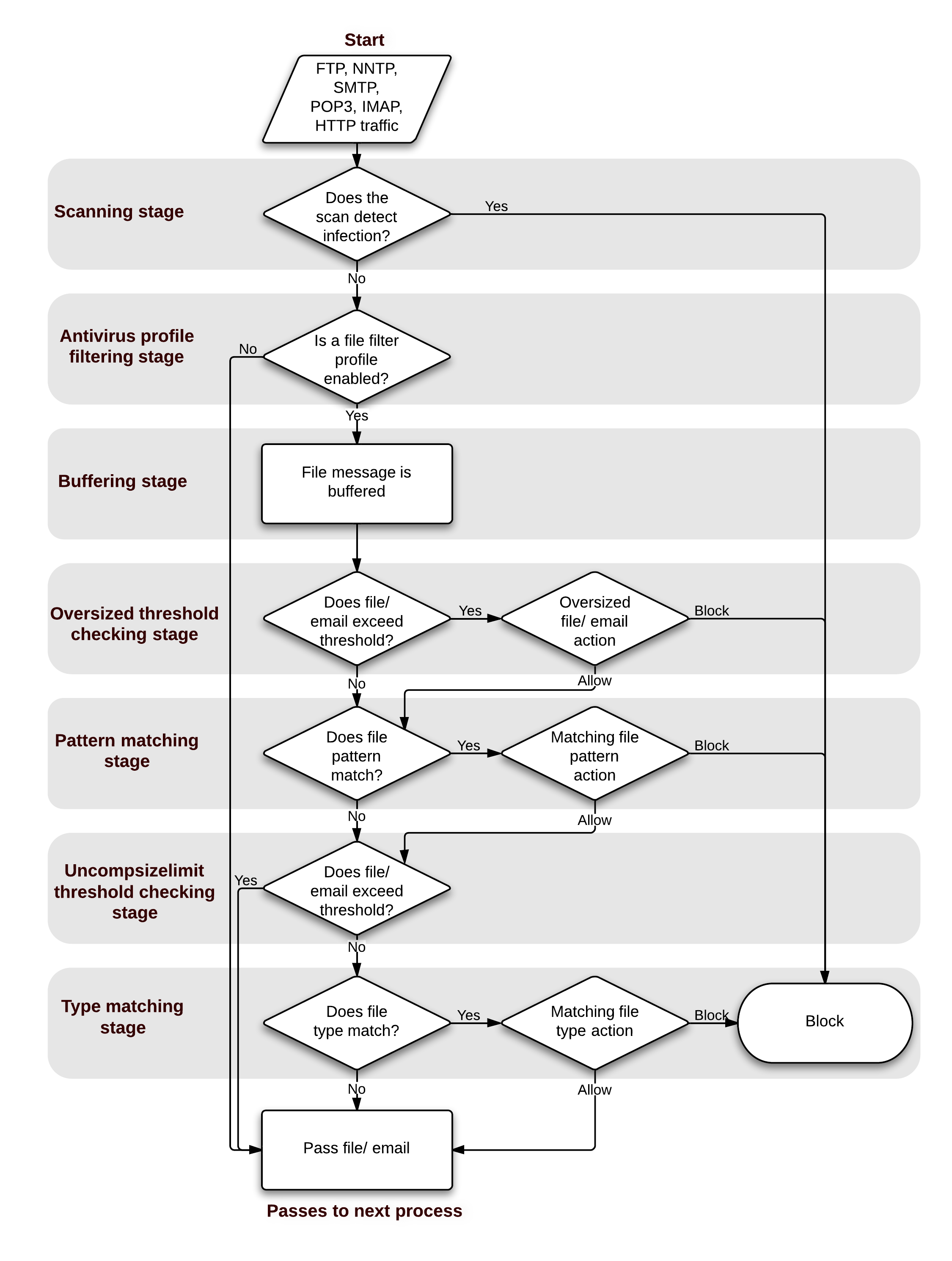
Antivirus scanning order when using the normal, extended, or extreme database
If a file fails any of the tasks of the antivirus scan, no further scans are performed. For example, if the file fakefile.EXE is recognized as a blocked file pattern, the FortiGate unit will send the end user a replacement message, and delete or quarantine the file. The unit will not perform virus scan, grayware, heuristics, and file type scans because the previous checks have already determined that the file is a threat and have dealt with it.
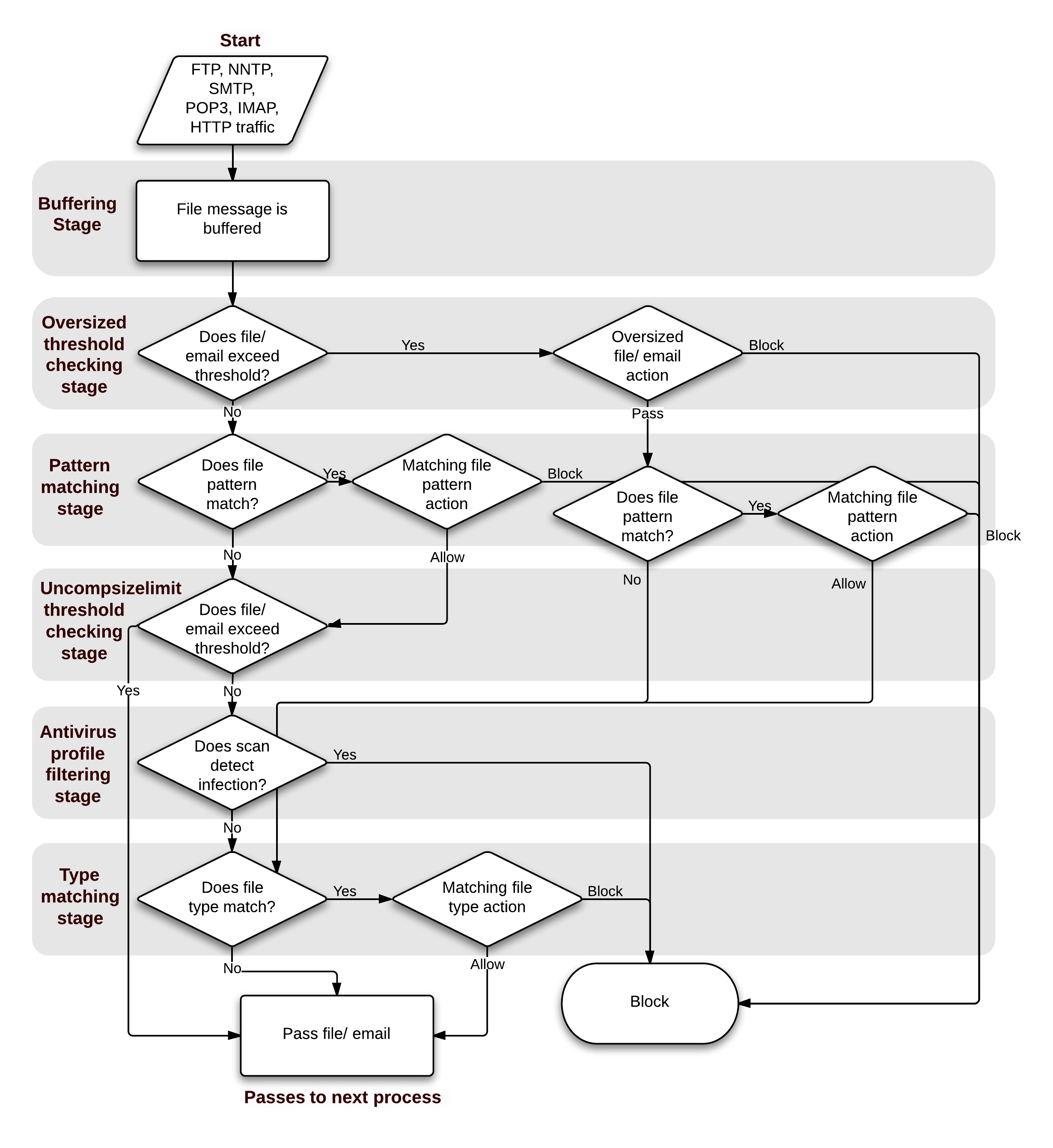
Flow-based antivirus scanning order
The following figure illustrates the antivirus scanning order when using flow-based scanning (i.e. the flow-based database). The antivirus scan takes place before any other antivirus-related scan. If file filter is not enabled, the file is not buffered. The antivirus scan includes scanning for viruses, as well as for grayware and heuristics if they are enabled.